Data Execution Prevention (DEP) is a security feature that helps prevent damage from viruses and other security threats by monitoring your programs to make sure they use system memory safely. If you choose to protect all programs, you can still turn off DEP for individual programs. If you suspect that a program does not run correctly when DEP is turned on, check for a DEP-compatible version of the program or an update from the software publisher before you change any DEP settings. Click Advanced System Settings.  If you are prompted for an administrator password or confirmation, If you are prompted for an administrator password or confirmation,type the password or provide confirmation. Under Performance, click Settings. Click the Data Execution Prevention tab, and then click Turn on DEP for all programs and services except those I select.
|
|
Alt + E — Opens the Edit menu
Alt + Enter — Opens the Properties window
Alt + F — Opens the File menu
Alt + F4 — Closes the current program
Alt + Print — Screen Takes a screen shot of the current window or program
Alt + Tab — Switches between the programs currently in use
CTRL+TAB — SWITCHES BETWEEN TAB IN DIALOG BOX,I.E 7
Ctrl + A — Selects all text
Ctrl + C — Copies the selected object
Ctrl + End — Jumps to the end of the current document
Ctrl + Esc — Opens the Start menu
Ctrl + F4 — Closes the current program
Ctrl + Home — Jumps to the beginning of the current document
Ctrl + Insert — Copies the selected object
Ctrl + left arrow — Moves to the left one word
Ctrl + right arrow — Moves to the right one word
Ctrl + V — Pastes the selected object
Ctrl + X — Cuts the selected object
Ctrl + the "+”key — Perfectly resizes the width of Explorer columns
End — Jumps to the end of the current line
F1 — Opens the Help menu
F2 — Renames the selected icon
F3 — Launches the Search Companion in a folder or on the
desktop
F4 — Accesses the Address Bar in a folder or window
F5 — Refreshes the contents of a folder or window
Home — Jumps to the beginning of the current line
Shift + Delete — Permanently deletes files (bypasses the Recycle Bin)
Shift + End — Highlights text from the current position to the end of
the line
Shift + F10 — Substitutes for a right-click
Shift + Home — Highlights text from the current position to the
beginning of the line
Shift + Insert — Pastes the selected object
Shift while inserting — Prevents the CD player from playing an audio CD
Shortcuts for Keyboards with a "Windows”Key (Resembling a Flag)
Windows Key + E — Opens Windows Explorer
Windows Key + F — Launches the Windows Search Companion
Windows Key + F1 — Opens the Help and Support Center
Windows Key + L — Locks down Windows
Windows Key + M — Minimizes all windows and shows the desktop
Windows Key + M + Shift — Undoes the minimize
Windows Key + Opens — the System Properties window
Pause/Break key
Windows Key + R — Opens the Run window
Windows Key + U — Launches the Utility Manager
WINDOWS KEY+U — MINIMIZES ALL WINDOWS AND GOES TO DESKTOP
|
1. Check Windows Update and Office Update regularly (http://office.microsoft.com/productupdates); Click on the Automatic Updates tab in the System control panel and choose the appropriate options. 2. Install a personal firewall. Both SyGate (www.sygate.com) and ZoneAlarm (www.zonelabs.com) offer free versions. 3. Install a free spyware blocker. I am choose SpyBot Search & Destroy (http://security.kolla.de). SpyBot is also paranoid and ruthless in hunting out tracking cookies. 4. Block pop-up spam messages by disabling the Windows Messenger service. Open Control Panel >> Administrative Tools >> Services and you'll see Messenger Right-click and go to Properties, Set Start-up Type to Disabled and press the Stop button. Bye spam pop-ups! 5. Use strong passwords and change them periodically. Passwords should have at least seven characters; use letters and numbers and have at least one symbol. 
6. If you're using Outlook or Outlook Express, use the current version or one with the Outlook Security Update installed. The update and current versions patch numerous vulnerabilities. 7. Buy antivirus software and keep it up to date. If you're not willing to pay, try AVG Free Edition 8. If you have a wireless network, turn on the security features: Use MAC filtering, turn off SSID broadcast, and even use WEP with the biggest key you can get.
|
I am going tell a trick by which you hide your Windows hard disk partitionwithout any use of software. For this trick I am use the MS DOS (Command Prompt).Microsoft make the MS DOS for Command Line Instruction.I think every person whose that usethe Windows know very well about Command Prompt. If we say about hackers,Windows registry(regedit) and MS DOS always favourite features in Windows. So.I am again use the MS DOS for hide the Windows Drive . 1: Go to 'RUN' and type 'cmd' by which command prompt open. Type 'Diskpart' and press ENTER key like given below...  By doing it Diskpart come into Global Configuration Mode. By doing it Diskpart come into Global Configuration Mode.2: Type 'list volume' like given below... By this you see all present partion of the Windows. 3:Type 'select volume _' in blank space you fill the partion drive alphabet which you want hide.For example i am choose the partion 'E' like given below... You see a astrix in front of choose partion which means your selection lock. 4: Type 'remove letter _' fill the blank space with selected partion alphabet,In my case i am write 'E' like given below picture... After press Enter Key you see message of successfully remove drive, given next command 'list volume' and it shown the hide partion like above picture.You go to MyComputer and see the hide drive. 5: For found the hide partion type 'assign letter _' in place of blank type the choose partition alphabat and press Enter Key,in my case i am write 'E' like given below...
 ...
Read more »
...
Read more »
|
Autoplay is the feature in Windows operating systems which lets you decide what application to use when you insert a media or device (USB or CD, CD, DVD etc.) to your computer. It also lets you set a default action for certain devices or medias.

It is good feature of Win7 but some time it come with problem.A virus with 'autorun' in the pen drive is too harmfull ,WHY?,when you insert a pen drive(also contain virus) then autoplay come with it when you insert the pen drive, autorun file of virus also start doing work and virus come on your system before you doing scan on the pen drive.For stop it,it is necessary to turn off the autoplay option for security purpose.For turn off the autoplay follow step given below...
- Click Start.
- In the Search field, type gpedit.msc and press Enter.
- The Local Policy Group Editor should appear on your screen.
- On the left pane go to Computer Configuration –Administrative Templates– Windows Components and clickAutoPlay Policies.
- On the right pane, click Turn Off Autoplay.
- Select Enabled and under Options, select where you want toturn off AutoPlay. (All drives or CD-ROM and removable media drives.)
- Click OK for the changes to take effect.
|
Today,I am tell about a common method by which you check that yourantivirus work properly or not.

Open Notepad and copy the Code given below.
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
It is a standard text developed by the European Institute for Computer Anti-virus Research (EICAR). Every Anti-Virus is programmed to load this file as a virus.
Save as this file by checkantivirus.com
It is not necessary you save this file by given name but use only this extension..
.com
After some seconds saving this file, your Anti-Virus should come with themessage that this file is infected with virus asking permission for its deletion/clean.
This file is secure and it is not going to any infect in your system.
If your antivirus remove this file then it is doing work properly otherwise you update your antivirus.
|
AVG Anti-virus is a good software which that protect your system by virus,malware and spam. You download this anti-virus from here
And instal it.

But you see this Anti-virus is a trial virson and allow you for use only 1 month .For making it license version ,we given you a serial number by which you register your trail version and valid it upto 2018. Serial number given below...
|
What cloud computing really means
Cloud computing comes into focus only when you think about what IT always needs: a way to increase capacity or add capabilities on the fly without investing in new infrastructure, training new personnel, or licensing new software. Cloud computing encompasses any subscription-based or pay-per-use service that, in real time over the Internet, extends IT’s existing capabilities.
Cloud computing is at an early stage, with a motley crew of providers large and small delivering a slew of cloud-based services, from full-blown applications to storage services to spam filtering. Yes, utility-style infrastructure providers are part of the mix, but so are SaaS (software as a service) providers such as Salesforce.com. Today, for the most part, IT must plug into cloud-based services individually, but cloud computing aggregators and integrators are already emerging.
InfoWorld talked to dozens of vendors, analysts, and IT customers to tease out the various components of cloud computing. Based on those discussions, here’s a rough breakdown of what cloud computing is all about:
1. SaaS
This type of cloud computing delivers a single application through the browser to thousands of customers using a multitenant architecture. On the customer side, it means no upfront investment in servers or software licensing; on the provider side, with just one app to maintain, costs are low compared to conventional hosting. Salesforce.com is by far the best-known example among enterprise applications, but SaaS is also common for HR apps and has even worked its way up the food chain to ERP, with players such as Workday. And who could have predicted the sudden rise of SaaS ”desktop” applications, such as Google Apps and Zoho Office?
2. Utility computing
The idea is not new, but this form of cloud computing is getting new life from Amazon.com, Sun, IBM, and others who now offer storage and virtual servers that IT can access on demand. Early enterprise adopters mainly use utility computing for supplemental, non-mission-critical needs, but one day, they may replace parts of the datacenter. Other providers offer solutions that help IT create virtual datacenters from commodity servers, such as 3Tera’s AppLogic and Cohesive Flexible Technologies’ Elastic Server on Demand. Liquid Computing’s LiquidQ offers similar capabilities, enabling IT to stitch together memory, I/O, storage, and computational capacity as a virtualized resource pool available over the network.
3. Web services in the cloud
Closely related to SaaS, Web service providers offer APIs that enable developers to exploit functionality over the Internet, rather than delivering full-blown applications. They range from providers offering discrete business services — such as Strike Iron and Xignite — to the full range of APIs offered by Google Maps, ADP payroll processing, the U.S. Postal Service, Bloomberg, and even conventional credit card processing services.
4. Platform as a service
Another SaaS variation, this form of cloud computing delivers development environments as a service. You build your own applications that run on the provider’s infrastructure and are delivered to your users via the Internet from the provider’s servers. Like Legos, these services are constrained by the vendor’s design and capabilities, so you don’t get complete freedom, but you do get predictability and pre-integration. Prime examples include Salesforce.com’s Force.com,Coghead and the new Google App Engine. For extremely lightweight development, cloud-basedmashup platforms abound, such as Yahoo Pipes or Dapper.net.
5. MSP (managed service providers)
One of the oldest forms of cloud computing, a managed service is basically an application exposed to IT rather than to end-users, such as a virus scanning service for e-mail or an application monitoring service (which Mercury, among others, provides). Managed security services delivered by SecureWorks, IBM, and Verizon fall into this category, as do such cloud-based anti-spam services as Postini, recently acquired by Google. Other offerings include desktop management services, such as those offered by CenterBeam or Everdream.
6. Service commerce platforms
A hybrid of SaaS and MSP, this cloud computing service offers a service hub that users interact with. They’re most common in trading environments, such as expense management systems that allow users to order travel or secretarial services from a common platform that then coordinates the service delivery and pricing within the specifications set by the user. Think of it as an automated service bureau. Well-known examples include Rearden Commerce and Ar
...
Read more »
|
Today,i am going to tell you how to genuine your unregistered windowsOS,by which you found the latest update from Microsoft and enhance the security and other features of the Windows. This work for the Windows Vista and 7 . Open the tool you see a window like given below... 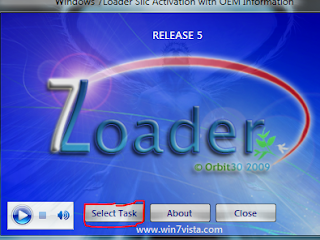
Click on the 'Select Task' and you see the new window like given below... 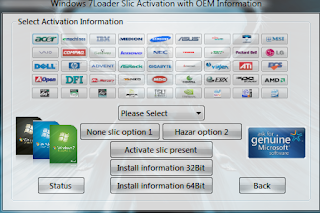 Go to 'Please Select' option and choose your any brand name. After that Click on the "Activate slic Present" and Wait after some time a new window open just choose anything. After doing that click on 'Install information 32bit' or 'Install information 64bit' according to your operating system. Now click 'Hazar option 2' after some time a option come for restart your computer ,then reboot your system. Go to MyComputer property and check,your OS done genuine.
|
Yahoo! Messenger is an instant messaging program which is compatiblewith all Windows versions. While instant messaging is the focus of Yahoo!Messenger, there are several special tricks that can enhance the user experience. Here are my 10 Best Yahoo! Messenger Tricks and Hacks: 1. Find invisible users on your Yahoo! Messenger list Want to find out someone who’s hiding from you? You can easily do so by going to Yahoo! Invisible Checker. All you need to do is type in the Yahoo! ID and the particular users status will be revealed. 2. Invisible nickname on chat rooms Just go to edit profile and in the nick name type a (space character) on it just press Alt 0160 ( or ALT+255 ) and save it. Now go to any Yahoo! chat room and you’ll notice that your nick name is empty. [ Alt+0160 is a keyboard shortcut for space] 3. Run Multiple Instances of Yahoo! Messenger on same system Some of you might be having more than one Yahoo! ID would like to log in simultaneously. Here is an easy way to do it without installing any sort of software. You just have to edit the registry and voila there you go. Follow the instructions below: - Download the following -multiyahoo.reg and save it to your hard disk.
- Double click on it.
 - The above dialog will popup, click ‘Yes’
- Start the yahoo messenger login with your first ID. Then again start another yahoo messenger by clicking on the messengericon and log in with your second ID.This tweak works with all versions of Yahoo Messengers.
4. Removing Ads from your Yahoo! Messenger If you are using Yahoo! Messenger 8.0, then you can disable ads by following the below steps: - First close the Yahoo! Messenger.
- Save this .bat file and execute it. (Note: You won’t be able to enter the chat rooms if you use this patch.)
The above fix doesn’t work for Yahoo! Messenger 9 Beta. Here’s a way to disable the ads in Yahoo! Messenger 9: - Make sure the Yahoo! Messenger isn’t running, if it is then just close it.
- Now backup the following file C:\Program Files\Yahoo!\Messenger\Yahoo!Messenger.exe (create a new copy)
- Download HxD hex editor.
- Open C:\Program Files\Yahoo!\Messenger\Yahoo!Messenger.exe in the hex editor
- Now go to the offset 295928 (in HxD: Search/
...
Read more »
|
Malware, short for malicious software, is software designed to secretly access a computer system without the owner's informed consent. The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code.The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware, including true viruses. [Wikipedia]
With the increase in malware "programmers", numerous malwares/spywares are releasing everyday.
Here are some ways to stay safe from most malwares in Windows:
1. OS Installation Directory
Most of them are skids, so they hard-code location names in their apps, instead of getting the System Directory. As you know the default installation of Windows XP, Vista, 7 is C:\Windows. When you are installing an OS, you are asked for the installation location, even Directory name. Just change C:\Windows to something like E:\OSdir, etc. and you should be immune from skid malwares.
Note: Some softwares may stop working this way, since it can be possible that they are using the same idea. Just find an alternative for them.
2. Show Hidden Folders, and System Files
It is really easy to make any file System/Hidden in most programming languages, so most malwares hide their stub using these attributes. It becomes real easy to find them after you unhide them.
3. Use BinText on suspicious apps
You have found a suspiciously hidden App? Open it in BinText, it will display all Text in the app. Most programmers don't hide Text, although it can be done by obfuscating. But there is still a very good chance you can find suspicious information in an app. If you find text like "
...
Read more »
|
Let’s say you are chatting on msn, and someone you don't know is starting a conversation with you. If you want to know from where is the person you are chatting with, or check if she/he is telling the truth, you can trace the location (country, city, etc. ), and IP Address of the person. There are several methods of doing it but here’s an easy one. The only thing you have to do is to actually make the person click a link you send him. When that person clicks the link, you will receive information like IP Address, Country, Host name, Operating System /Browser Details and region name. Just follow instructions below: 1. Visit this link and enter your email id in it. You will receive your trace reports in it. 2. You will receive a unique link in your inbox like this http://acmepeers.com/?u=vyg (Mostly its in Spam Folder) 3. When someone clicks that link you will receive tracing reports to your email . You can click the above link yourself to check the accuracy of the system by tracing yourself. It looks like this: 
|
Who doesn’t like free stuff! I know you do, that’s why I’m going to give you this awesome system optimization tool - Advanced SystemCare Pro. In my personal opinion, IObit products especially the latest Advanced SystemCare PRO is my favorite and BEST system tuning software to keep my computer running like new. It provides an always-on, automated, all-in-one PC Health-care Service with anti-spyware, privacy protection, performance tune-ups, and system cleaning capabilities. This powerful and award-winning precision tool fixes stubborn errors, cleans out clutter, optimizes Internet and download speeds, ensures personal security, and maintains maximum computer performance automatically.
Here i am giving you a free serial key for Advanced SystemCare Pro Edition.

Have a great time using your Advanced SystemCare Pro.
|
Shorten the time it takes for your desktop to appear when you turn on your PC and make XP shut down faster as well.
In some cases computers running with Windows XP takes too much time to shutdown and  repeatedly annoy users with pop up messages asking if you really want to quit the applications. This problem is mainly due to applications that installservices that start at Windows XP boot time and then take a very long time to stop and sometimes time out whenWindows is being shut down. No matter how fast your PC shuts down, it's not fast enough. This tweak reduces the time Windows-XP waits before automatically closing any running programs when you give it thecommand to shutdown. repeatedly annoy users with pop up messages asking if you really want to quit the applications. This problem is mainly due to applications that installservices that start at Windows XP boot time and then take a very long time to stop and sometimes time out whenWindows is being shut down. No matter how fast your PC shuts down, it's not fast enough. This tweak reduces the time Windows-XP waits before automatically closing any running programs when you give it thecommand to shutdown.
How to Improve Your Computers Shutdown And Reboot Speed?
For speeding up your shutdown and reboot time in Windows XP, you need to edit some registry settings. Follow the steps as given below:
1. Go to Start then select Run
2. Type 'Regedit' and click ok

3. Find 'HKEY_CURRENT_USER\Control Panel\Desktop\'
4. Select 'WaitToKillAppTimeout'
5. Right click and select 'Modify'

6. Change the value to '1000'
7. Click 'OK'

8. Now select 'HungAppTimeout'
9. Right click and select 'Modify'
![]() ...
Read more »
...
Read more »
|
I'll make it short. I found this out on myself just by peeping around and Googling a bit.
1. Open Firefox.
2. Clear your cache.
Open Firefox and select "Tools" -> "Options", select the Advanced panel, and click on the Network tab. In the Offline Storage section, click Clear Now.

Click OK to close the Options window
3. Load the web page that contains your flash video. Make sure it streams all the way. This means you now have it in your computer's cache.
4. Open a new tab and write "about:cache" in the address bar (without the "quotes").

5. Under "Disk cache device", copy the path shown for the cache directory.

6. Paste that path in My Computer, or navigate to it however you want.
7. Order files by size.
8. The biggest file should be your video. It's going to have a weird name like 54DDEA30e01 but that's fine. This is your video.
9. Open the file with a media player that supports the format, such as VLC Player.
NOTE: Most likely, your computer won't know which software to run this file type with, so just select "open file with" option after clicking the file with the secondary mouse button, and choose VLC Player.
|
this tweak removes the context menu that would normally appear whenthe user right clicks on the desktop or in the Explorer right results.
Previously I posted a tutorial How to disable "Turn off Computer" button on start menu. In this post i want to show you how to disable the right click functionality on desktop and explorer by using a simple registry hack. The bad thing is that people can still drag files and folders and drop them everywhere but it does provide some level of protection.
Lets start:
To use this feature, you will need to be logged into your computer withadministrative rights.
1. Go to Start > Run > type REGEDIT and hit enter. Navigate to:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer

2. Here in right side panel, right click to create a new DWORD value with the name NoViewContextMenu (it is case sensitive), then assign number 1 in value data box.

Adding the registry tweak above will disable mouse right click for ALL users. If you only want to disable for the current logged in user, you should add the registry tweak to HKEY_CURRENT_USER instead of HKEY_LOCAL_MACHINE.
|
Basically this technique is called SAFE-TEXT. It's a technique where a message destroys itself after being read. If you want to call it the Data-centric Suicide Message, that's fine too. This is a website that allows you to send such type of sms for free of cost after registering on it. But it has limitation that you can send only 10 SMS a day.
So here's the thing. With Wikileaks on one side and British libel law on the other, there's room for a tool that lets you say what needs to be said, but without it falling into the wrong hands in the process.
What it does is allow you to send an expletive-laden opinion of your boss to a co-worker, or an it's-in-the-public's-interest-to-know-this leak to your friend on the Guardian (or Wired), without it having a chance to be read by said boss, or unsaid MP.
Note: This trick should only work for British mobile network operators.
Here’s how to use it:
- To register and activate, text WIRED to 83118 (charged at your standard network rate). You’ll be able to send up to 10 messages daily.
- If you’re the sender, the message will show your name and number.
- Write your libel-ridden hate speech and hit send.
- The receiver will then be sent a text telling them they have been sent a Wired Safe Text with a link to the mobile internet site that hosts your message.
- When they click through they will activate Safe Text. They will only have a few seconds to read the text (so don’t make it too long) before it self-destructs.
|
Now all of you know that Photoshop is the heavyweight champ in the image-editing category, but most people don’t need such an advanced toolset for everyday image-editing tasks, and its price is near $650. In this post i'll show you some of the best free image editors that are so easy to use.
1. IrfanView - IrfanView is probably the most popular and feature packed free image viewer  for Windows that can view, edit, and convert image files and play video/audio formats. It has been around for many years and keeps getting better. In addition to standard image viewing, it includes many additional features including slideshow, batch conversion, image adjustment, image editing, resizing, panorama stitching, auto EXIF rotation and more. There certainly are more user-friendly and attractive image viewers, but few that offer all the functionality, and extendibility that IrfanView can provide. for Windows that can view, edit, and convert image files and play video/audio formats. It has been around for many years and keeps getting better. In addition to standard image viewing, it includes many additional features including slideshow, batch conversion, image adjustment, image editing, resizing, panorama stitching, auto EXIF rotation and more. There certainly are more user-friendly and attractive image viewers, but few that offer all the functionality, and extendibility that IrfanView can provide.
2. Paint.NET - Paint.NET features an intuitive and innovative user interface with support for  layers, unlimited undo, special effects, and a wide variety of useful and powerful tools. An active and growing online community provides friendly help, tutorials, and plugins. Many special effects are included for enhancing and perfecting your images. Everything from blurring, sharpening, red-eye removal, distortion, noise, and embossing are included. Also included is our unique 3D Rotate/Zoom effect that makes it very easy to add perspective and tilting. I am using this software and it's really great. layers, unlimited undo, special effects, and a wide variety of useful and powerful tools. An active and growing online community provides friendly help, tutorials, and plugins. Many special effects are included for enhancing and perfecting your images. Everything from blurring, sharpening, red-eye removal, distortion, noise, and embossing are included. Also included is our unique 3D Rotate/Zoom effect that makes it very easy to add perspective and tilting. I am using this software and it's really great.
3. FastStone Image Viewer - FastStone Image Viewer is a fast, stable, user-friendly image  browser, converter and editor. It has a nice array of features that include image viewing, management, comparison, red-eye removal, emailing, resizing, cropping, color adjustments, watermarks and more. FastStone Image Viewer supports all major graphic formats including BMP, JPEG, JPEG 2000, GIF, PNG, PCX, TIFF, WMF, ICO and TGA as well as digital RAW formats including CRW, CR2, NEF, PEF, RAF, MRW, ORF and DNG). browser, converter and editor. It has a nice array of features that include image viewing, management, comparison, red-eye removal, emailing, resizing, cropping, color adjustments, watermarks and more. FastStone Image Viewer supports all major graphic formats including BMP, JPEG, JPEG 2000, GIF, PNG, PCX, TIFF, WMF, ICO and TGA as well as digital RAW formats including CRW, CR2, NEF, PEF, RAF, MRW, ORF and DNG).
4. GIMP - GIMP (GNU Image Manipulation Program) is specifically a raster graphics editor  used to process digital graphics and photographs. It is usually the direct free replacement for Photoshop and rightly so, there are very few limitations, its very powerful, and is probably easier to use than Photoshop. With its dedicated community you can find all the help, tutorials and plugins you would ever need. All this for free! used to process digital graphics and photographs. It is usually the direct free replacement for Photoshop and rightly so, there are very few limitations, its very powerful, and is probably easier to use than Photoshop. With its dedicated community you can find all the help, tutorials and plugins you would ever need. All this for free!
OS : Windows ALL, Mac OS X, and SkyOS.
5. Photoscape - PhotoScape is a complete photo editing suite that  includes image browsing/viewing, photo editing, picture page printing, photo resizing and renaming, and even RAW conversion. It is a very complete package that will meet most of your digital image editing needs. includes image browsing/viewing, photo editing, picture page printing, photo resizing and renaming, and even RAW conversion. It is a very complete package that will meet most of your digital image editing needs.
|
Hacking passwords or any information using USB pendrive. Learn how to steal information or passwords of your friends or enemies usingpendrives...
 Today I will show you how to hack Passwords usingUSB Pen Drive. As we all know, Windows stores most of the passwords which are used on a daily basis, including instant messenger passwords such as MSN, Yahoo, AOL, Windows messenger etc. Along with these, Windows also stores passwords of OutlookExpress, SMTP, POP, FTP accounts and auto-complete passwords of many browsers like IE and Firefox. There exists many tools for recovering these passswords from their stored places. Using these tools and an USB pendrive you can create your own rootkit to hack passwords from your friend's/college Computer. We need the following tools to create our rootkit. Today I will show you how to hack Passwords usingUSB Pen Drive. As we all know, Windows stores most of the passwords which are used on a daily basis, including instant messenger passwords such as MSN, Yahoo, AOL, Windows messenger etc. Along with these, Windows also stores passwords of OutlookExpress, SMTP, POP, FTP accounts and auto-complete passwords of many browsers like IE and Firefox. There exists many tools for recovering these passswords from their stored places. Using these tools and an USB pendrive you can create your own rootkit to hack passwords from your friend's/college Computer. We need the following tools to create our rootkit.
MessenPass: Recovers the passwords of most popular Instant Messenger programs: MSN Messenger, Windows Messenger, Yahoo Messenger, ICQ Lite 4.x/2003, AOL Instant Messenger provided with Netscape 7, Trillian, Miranda, and GAIM.
Mail PassView: Recovers the passwords of the following email programs:Outlook Express, Microsoft Outlook 2000 (POP3 and SMTP Accounts only), Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts), IncrediMail, Eudora, Netscape Mail, Mozilla Thunderbird, Group Mail Free.
Mail PassView can also recover the passwords of Web-based email accounts (HotMail, Yahoo!, Gmail), if you use the associated programs of these accounts.
IE Passview: IE PassView is a small utility that reveals the passwords stored by Internet Explorer browser. It supports the new Internet Explorer 7.0, as well as older versions of Internet explorer, v4.0 - v6.0
Protected Storage PassView: Recovers all passwords stored inside the Protected Storage, including the AutoComplete passwords of Internet Explorer, passwords of Password-protected sites, MSN Explorer Passwords, and more…
PasswordFox: PasswordFox is a small password recovery tool that allows you to view the user names and passwords stored by Mozilla Firefox Web browser. By default, PasswordFox displays the passwords stored in your current profile, but you can easily select to watch the passwords of any other Firefox profile. For each password entry, the following information is displayed: Record Index, Web Site, User Name, Password, User Name Field, Password Field, and the Signons filename.
Here is a step by step procedre to create the password hacking toolkit.
NOTE: You must temporarily disable your antivirus before following these steps.
1. Download all the 5 tools, extract them and copy only theexecutables(.exe files) into your USB Pendrive.
...
Read more »
|
I've been using Nero all the time and in my opinion it's the best software to write CD and DVD. But there are so many free softwares which help you to do the same. Here is my list of top 10 free burning softwares that you can use in place of Nero.
1. ImgBurn - ImgBurn is probably the best free CD/DVD burning tool available. ImgBurn can write most types of CD / DVD images including BIN, DI, DVD, GI, IMG, ISO, MDS, NRG and PDI. ImgBurn supports all the Windows OS’s – Windows 95, 98, Me, NT, 2000, XP, 2003 and Vista (including all the 64-bit versions). If you use Wine, it should also run on Linux and other x86-based Unixes.
2. CDBurnerXP - CD Burner XP is a great software. Apart from CDs and DVDs, you can also burn Blu-Ray and HD-DVDs with it. It also includes the feature to burn and create ISOs, as well as a Multilanguage interface.
Operating Systems supported- Windows 2000/XP/2003 Server/Vista.
3. InfraRecorder - Infra Recorder can burn CD, DVD, Dual Layer DVDs and also supports various audio formats. The audio and data tracks includes .wav, .wma, .ogg, .mp3 and .iso formats. It can erase rewritable discs. Infra Recorder can also burn images in ISO and BIN/CUE formats.It supports multisession writing of discs.
4. Express Burn - Express Burn is a free CD burning program that lets you create and record audio and data CDs under Windows and Mac OS X. This software has a great user friendly interface. To use it all you need to do is drag and drop files. One thing surprises me; well I don’t know how far it’s true; the makers of this software claim that Express Burn is the fastest CD/DVD writing program in the world using proprietary optimizing systems.
5. FinalBurner Free Edition - FinalBurner is one more top free burning software. It can create data, audio and video discs. It can burn CD R/RW, DVD+R/RW, DVD-R/RW, and DVD DL. It can also rip Audio CD in .wav, .mp3, .ogg, .mid, .wma, .aac, .mp4, .m4a, .xm, .mod, .s3m, .it, .mtm, .mo3audio files. FinalBuner can burn Video DVD with formats AVI, DIVX, XVID, MP4, MPG, WMV, ASF, MOV, FLV, etc. FinalBurner can also create an ISO image of a disc.
6. Ultimate CD/DVD Burner - Ultimate CD/DVD Burner is a simple and easy to use CD and DVD burning software package. It supports a very wide range of internal and external (USB 2.0 and FireWire) CD and DVD writers. Burn any data, copy any disc, make backups, create astonishing photo CD albums, make ISO CDs with this very easy to handle software!
7.
...
Read more »
| |

























